Introduction to OPSEC (Part 1)
Preface.
In today’s interconnected world, operational security (OPSEC) is of greater importance than ever before. OPSEC, a process traditionally associated with military and intelligence operations, has evolved into a critical component of digital security, privacy, and personal safety. However, the understanding and implementation of OPSEC procedures are often fragmented, despite its widespread usage across industries based on well-defined frameworks such as NIST. From corporate environments to individuals managing their digital hygiene, each sector tailors OPSEC to address its unique challenges and priorities. This divergence creates knowledge gaps regarding the process of Operational Security.
I personally feel that there is a lack of exposure and even more, an oversimplification or an overcomplication on what OPSEC per se is.
“He had a bad OPSEC and that’s why he got caught! If he followed X guide with the right tools maybe he could’ve gotten away”
He would’ve delayed his capture, but he could’ve never gotten away. (either arrested, or worse…)
OPSEC is not just about “do not do this or that”; it is a process where one must understand the risks involved with every action taken, digitally and physically. OPSEC is not about having a ‘Get Out of Jail Free’ card for every situation. It is a mindset, likened to knowing that just because one wears a hoodie and sunglasses in broad daylight doesn’t make them instantly anonymous except in highly specific movie scenes. The tiny things, the stuff seemingly too irrelevant, get you caught eventually.
This fragmentation becomes particularly concerning when considering groups in the hacker community, activists, or anyone operating under adversarial conditions, such as facing surveillance from adversary governments or malicious entities. Poor OPSEC in such contexts can prove catastrophic, with consequences ranging from exposure of identities to legal repercussions, reputational damage, or even physical harm. Despite its critical importance, OPSEC remains a concept that is often misunderstood, overly abstract, or inadequately communicated to those who need it most.
Our objective is to tailor the OPSEC process by analyzing the building blocks: what critical information needs protection, what specific threats such as adversaries or environmental risks exist, what vulnerabilities exist in personnel, processes, or technology, and what countermeasures can be implemented to mitigate identified risks. This involves making continuous observations while revising the measures over time to ensure continued resilience against emerging threats.
We will explore how such concepts can be applied across a wide range of industries, from companies, intelligence agencies, personal privacy and maybe talking a bit about finance (especially in the upcoming articles).
This series of articles wants to address the lack of clear and coherent OPSEC doctrine in infosec contexts. Many existing resources are plagued by over-technical explanations, context-less directives, or niche scenario focuses, making them inaccessible to the very people they’re meant to protect.
This series has two key objectives:
- Demystify OPSEC for readers who are new to the concept.
- Provide both theoretical and practical guidance for its implementation.
By analyzing common OPSEC failures within the hacking community, arguably one of the groups most at risk of surveillance, we can derive lessons applicable across various domains. Through this broad introduction, we aim to consolidate fragmented perspectives on OPSEC, equipping readers with actionable strategies to mitigate risks, safeguard sensitive information (whether it’s nuclear missile codes or personal life details), and try to regain control over their digital and physical security.
Moreover, these articles are not reserved for experts, they are intended for anyone navigating a world where information shapes reality and survival depends on protecting that information. Through clear and straightforward explanations, I hope to make both the theoretical and technical aspects of OPSEC accessible to all.

An Introduction to Operational Security.
The Purple Dragon operation during the Vietnam War laid the basis for Operations Security, a methodical process to stop the unintentional revelation of critical information to adversaries. Originated from U.S. military defeats attributed to operational data leaks, Purple Dragon showed very vividly that adversaries often gained intelligence not through espionage but by observing patterns in routine activities. This realization inspired a revolution in the way security vulnerabilities were perceived and mitigated, ultimately leading to the realization of an official OPSEC methodology.
During the Vietnam War, operations such as Rolling Thunder and Arc Light were seriously compromised because enemy forces knew when and where strikes were going to occur and planned accordingly. Investigations into how this foreknowledge occurred determined that, in many cases, it was due to a pattern of troop movements, supply logistics, and non-encrypted communications. In response to these findings, the Joint Chiefs of Staff initiated Purple Dragon, bringing together experts in intelligence, communications security, and counterintelligence.
The Purple Dragon team analyzed operations from top to bottom, finding the “small clues” that adversary compiled. For example, supply convoys running on a schedule, or notifications to friendly pilots regarding planned airstrikes, served as unintended warnings. The team made it clear that security is a process, not an activity, and the output of their efforts became the formalized OPSEC process.
The NSA-backed research showed that apparently normal activities such as troop movements or radio communications could reveal important intelligence if a pattern could be discerned over time. For example, how frequently and at what time of the day supplies were delivered could give a fair indication of potential future operations. Building on this concept, Purple Dragon outlined a formal process to identify sensitive information and restrict access to it. The project team introduced a five-step process that would become OPSEC: “Systematic and proven process by which potential adversaries can be denied information about capabilities and intentions by identifying, controlling, and protecting generally unclassified evidence of the planning and execution of sensitive activities. The process involves five steps: identification of critical information, analysis of threats, analysis of vulnerabilities, assessment of risks and application of appropriate countermeasures.“
This brought a complete turnaround in military security. OPSEC formalized practices that military forces had used up until then in a less structured manner, keeping the critical details hidden from enemies. The insights from Purple Dragon set a basis for systematic identification of vulnerabilities, risk assessment and introduction of countermeasures.
Over time, these principles expanded beyond military use. Throughout the Cold War, OPSEC was essential to the intelligence operations; adversaries were continually pursuing weaknesses in the practices of each other. As technology continued to evolve, corporations took OPSEC concepts to ensure that trade secrets remained intact, and IT did so in efforts to keep sensitive data just that sensitive.
Purple Dragon and the OPSEC Process.
The results of the Purple Dragon codified the OPSEC process to protect sensitive information against military and security operations. In a clearly outlined and largely sequential five-step process, it covers vulnerabilities that may cause exposure:
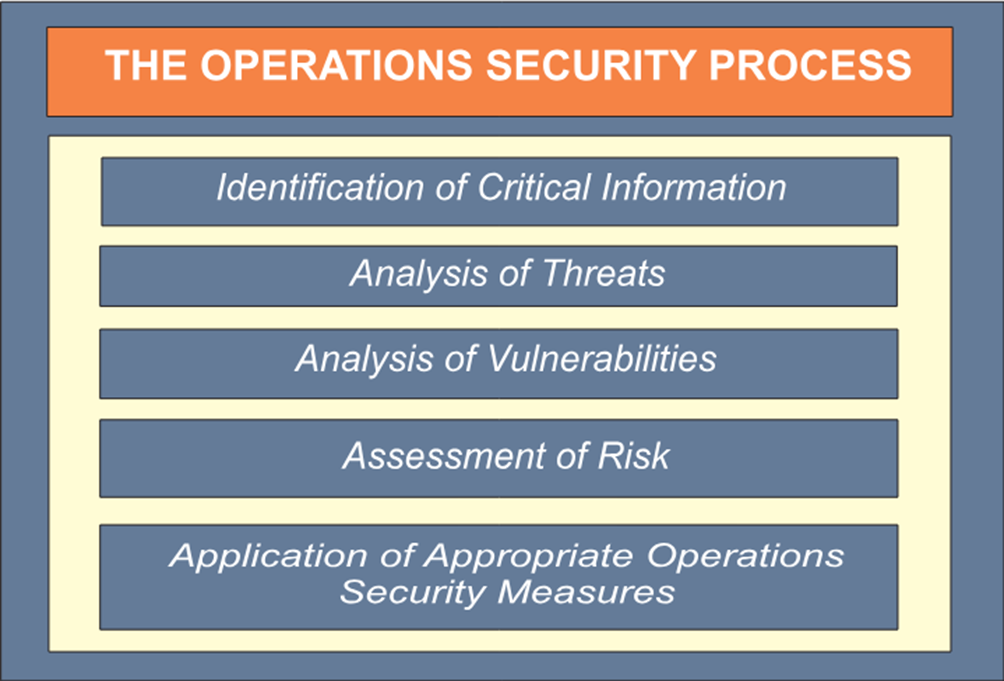
Identification of Critical Information: This is the fundamental step wherein critical information is defined as information that, if obtained by an adversary, can prove to be detrimental to any operation. In identifying such information as troop positions, movement plans, communication frequencies and so forth, much confusion on adversaries about military strategies is avoided. Where what constitutes “critical” is clearly defined, it enables organizations to concentrate their resources on the protection of truly valuable information and will not overextend resources on less impactful data.
Analysis of Threats: This is where an entity closely monitors capabilities, motives and intentions of would-be adversaries for any predictions regarding possible ways they may decide to attack. Effective threat analysis comprises gathering intelligence about adversaries regarding their technological capabilities, known tactics and historical patterns of behavior. For example, intelligence teams could study an adversary’s methods of electronic surveillance or analyze how they have ever laid hold of weaknesses, if at all, during similar operations. These threats offer the premise for articulating specific countermeasures which meet the known capabilities of an adversary and forestall reasonably predictable breaches of security.
Analysis of Vulnerabilities: This is a detailed examination of the weak points at which critical information is most likely to be exposed either under conditions of design or inadvertently. Vulnerabilities may occur via communications channels, transportation schedules, or perhaps through personnel behavior that an adversary could study over time. For instance, regular patterns in convoy movements could be used to ascertain logistics schedules, and communications conducted with open air radio could inadvertently broadcast sensitive plans. Through vulnerability analysis, organizations realize a clear view of all points at which their information could be at risk and thereby empower it to secure those weak spots.
Assessment of Risk: Once the vulnerabilities have been identified, it falls to the risk assessment to ascertain the likelihood and impact of each being exploited. This would include ranking threats according to the order of their likelihood and the potential damage they could cause in case an adversary successfully exploits them.
For example, high-risk vulnerabilities involving open lines of communication during sensitive operations will need immediate action. This helps organizations prioritize resources by focusing on high-impact, high-likelihood risks that could seriously compromise security if left unattended.
Application of Appropriate Operations Security Measures: Organizations will formulate and then implement security policies and preventive measures to mitigate the risk. These security countermeasures can range from changes in procedures, such as sending the convoys via different times to disrupt any degree of predictability, to technical solutions such as message encryption to avoid interception. People are also trained regarding these security protocols so that unintentional disclosures do not occur.
Evolution and Relevance of Operational Security, Frameworks in the Digital Landscape Today.
From its conceptualization and development in the military to secure sensitive information from adversaries, OPSEC today plays a particularly key role not only in national security but even in business, finance and personal privacy. In times where the world is surrounded by cyber threats, one needs to be more stringent with appropriate OPSEC frameworks than ever. These frameworks enable organizations and individuals to conceptualize their operations and maintain critical information from potential risks.
From Military to Digital: The Shift in Operational Security.
Traditionally, OPSEC was a military term describing a series of measures put in place to prevent adversaries from gathering information that would be valuable to them. The methodology involved the identification of critical information, assessment of associated threats, and application of countermeasures to safeguard the information. The principles of OPSEC, identify, analyze, and control risks to critical information, have now been adapted in a wide range of industries and especially in privacy, where the dangers of data breaches and other cyber-attacks can amount to catastrophes.
In today’s connected environment, threats are more sophisticated and multilayered. APTs, criminal organizations, and even states’ sponsored actors target organizations as much as individuals, making OPSEC a part of day-to-day operations. This concept has been made complicated in the digital age regarding the protection of online communications, cloud storage, and intellectual property, in addition to traditional concerns about physical security.
Basel II and Operational Security
The Basel Committee on Banking Supervision introduced the Basel II framework in 2004 to revamp how financial institutions manage risks, including those operational risks that affect an organization’s ability to function securely. Basel II revised the original Basel I agreement and focused on three key pillars: minimum capital requirements, supervisory review and market discipline. This regulation aimed at enhancing the resilience of banks through the identification, measurement, and management of their operational risks.
Basel II, in this respect, underlined the importance of not only physical asset protection but also the operational risks that would cause financial instability. These range from cyberattacks and fraud to business continuity problems that disturb daily operations. Basel II introduced the concept of managing these risks through comprehensive internal controls and risk management systems, ensuring that banks not only secure their financial data but also protect their operational processes.
Modern OPSEC Frameworks
With the advancement of security threats, different frameworks have been developed in recent times, taking note of the OPSEC process. These frameworks assist organizations in locating their vulnerabilities, taking measures for security, and further observing operations that might lead to potential risks. The most important and widely applied frameworks concerning OPSEC in the modern context include several well-established approaches.
Probably one of the most recognized frameworks to manage risks in cybersecurity is the Cybersecurity Framework (CSF) prepared by the National Institute of Standards and Technology. While this is not purely OPSEC focused, the five core functions of Identify, Protect, Detect, Respond, and Recover map to the fundamental principles of OPSEC. For example, the Identify phase requires an organization to identify and assess its critical information and vulnerability, a process directly related to the first step of OPSEC, which is the identification of critical information. The Protect phase is concentrated on safeguarding information from unauthorized access or any form of attack, a key concern of any OPSEC strategy. That makes this framework flexible and deep to ensure the continuity of operations for many industries in case of any kind of cyber threat.
The MITRE ATT&CK framework is a modern world OPSEC basic. It is a knowledge base that categorizes the tactics, techniques, and procedures that cyber adversaries use. MITRE ATT&CK allows organizations to understand, through attack-pattern analysis, the methods that attackers might use to compromise their operations and enables them to put in place measures to prevent such attacks. OPSEC practitioners make use of this framework to identify where their operations are vulnerable and how attackers may seek to compromise them. For instance, techniques like T1071, Application Layer Protocol, where the utilization of apparently harmless applications is used for hidden communications, can inform decisions on secure communication methods in OPSEC protocols.
ISO/IEC 27001 is an internationally accredited framework on the management of information security. It outlines how organizations should assess risks, establish security policies, and implement controls to protect sensitive data. Although it speaks to the overarching aspect of information security management, it borrows heavily from some critical ideas relative to OPSEC. It has placed great prominence on safeguarding operational processes and systems from internal information breaches or leaks and external attacks.
The Zero Trust model is increasingly being adopted to enhance security and OPSEC. Zero Trust operates on the principle that no entity, whether internal or external, should be automatically trusted. Instead, all users, devices, and systems must be continuously authenticated and authorized before gaining access to any resources. This model is in line with OPSEC because critical information and systems are kept safe from unauthorized access, even in cases where an attacker has breached the network. In practice, Zero Trust will involve least-privilege access, robust identity management, and micro-segmentation of networks.
Theoretical-Philosophical Application of OPSEC in Information Security for APTs: A Doctrine of Concealment.
How do Advanced Persistent Threats (APTs), and intelligence agencies operate?
The OPSEC Doctrine and Its Relevance to APTs
The core principle of OPSEC is simple: if something cannot be seen, it cannot be targeted, and if it cannot be found, it cannot be exploited. Experts and APTs understand that, in the digital world, revealing even the smallest amount of information creates potential vulnerabilities. The philosophy behind OPSEC dictates that APTs should not only protect their infrastructure but actively obscure their digital footprints. Their presence, when viewed through the lens of OPSEC, must be indistinguishable from the digital noise around them. The adoption of OPSEC within hacker culture, then, is about ensuring the invisibility of actions, infrastructure, and communications.
This approach, called “Security Through Obscurity” has deeply influenced the operational practices of intelligence agencies, who have used similar principles for decades to maintain secrecy and protect covert operations. Intelligence agencies understand that any visible signal whether through communication patterns, data leaks, or predictable behavior can be tracked, correlated, and ultimately exploited by adversaries. The integration of OPSEC into their work is therefore a means of rendering operations imperceptible, so that the adversary cannot even discern the existence of a threat.
Fragmentation of Information and Infrastructure
For APTs, the fragmentation of information is a fundamental aspect of OPSEC. This principle seeks to prevent an adversary from gaining a complete view of an operation by dispersing and isolating data. Intelligence agencies, when running covert operations, often employ a similar strategy. They disassemble the flow of information across multiple channels and devices, ensuring that no single point of compromise reveals the entirety of the operation.
In hacking, this fragmentation could manifest as the division of critical information across various encrypted communications channels. They may use multiple compromised systems to relay different pieces of information, ensuring that even if one part of the network is compromised, the rest remains protected. Similarly, APTs might break up their tools, malware, and communication patterns to obscure the true nature of their attack.
For intelligence agencies, this fragmentation prevents adversaries from building a coherent picture of a mission. By compartmentalizing information and limiting access to distinct parts of an operation, they ensure that even if one piece of the operation is discovered, it is of little value without the larger context. This segmentation prevents attackers from gathering enough data to understand the mission’s full scope.
This relates to the Identification of Critical Information.
Temporal Obfuscation: Breaking Predictable Cycles
In the context of OPSEC, temporal obfuscation refers to the practice of breaking predictable cycles of activity something APTs do to avoid detection. Intelligence agencies have long used this principle to avoid creating patterns that might give away their presence. APTs, too, use temporal obfuscation to prevent the adversary from predicting when an attack might occur or when a system might be used. This can be seen in the irregularity of actions taken, such as choosing to launch attacks at unpredictable times or sending communications during random intervals.
For APTs, breaking temporal patterns might involve delaying attacks or altering the timing of key actions. For example, rather than executing an exploit at a predictable time after infiltrating a network, an APT might wait days or weeks before moving further into the system. This randomness complicates efforts to track and trace the activities of threat actors, making it harder for defenders to predict or defend against their next move.
Intelligence agencies use temporal obfuscation in much the same way. Covert operatives avoid setting regular schedules that could be tracked by adversaries, making sure that their activities occur at irregular intervals and without clear patterns. This unpredictability ensures that the adversary cannot easily detect the rhythm of operations and prevents patterns from emerging that might reveal an intelligence operation.
This relates to Threat Analysis.
The Principle of Subtraction: Reducing the Footprint
Subtraction is another key principle of OPSEC that has direct relevance to APTs and intelligence agencies. In a digital context, subtraction refers to reducing visible signals that could be exploited by adversaries. APTs, like intelligence agencies, need to ensure that their presence on a network or within a system is as minimal as possible. This means using low-profile tools, avoiding actions that would trigger alerts, and ensuring that the systems they use do not create detectable signatures.
Intelligence agencies understand that any visible footprint whether it’s a communication signal, a transaction, or a piece of physical evidence can be tracked and linked back to them. This principle of reduction is embedded in their operations, where operatives are trained to leave as few traces as possible. Similarly, APTs operating under the principles of OPSEC will seek to minimize the visibility of their actions. By using tools that erase logs, employing encrypted communication channels, and avoiding actions that would leave a digital trail, they ensure that their activities remain undetectable.
For APTs, this means not only using secure communication channels but also ensuring that their malware or tools are highly stealthy and leave no trace after use. Any unnecessary visibility could tip off the defenders, giving them the time and information they need to react. The reduction of the digital footprint is therefore an essential aspect of ensuring the success of any operation, whether for APTs or intelligence agencies.
This relates to Vulnerability Analysis.
Defense in Depth and Encryption
Encryption is a critical tool in any APT’s OPSEC arsenal. However, as intelligence agencies have shown, encryption must go beyond simply securing communications. In the context of OPSEC, encryption is part of a larger strategy to create multiple layers of concealment. Persistent threats use encryption to protect both data at rest and in transit, ensuring that even if an adversary intercepts the data, it cannot be read. But OPSEC takes this further by layering encryption with other techniques, such as traffic masking, to hide the true nature of communications or data transfers.
For intelligence agencies, encryption is similarly used to protect sensitive information, but it is combined with other methods of concealment such as the use of decoys or the manipulation of metadata to make the real communication or data transfer unrecognizable. In the same way, APTs will use encryption alongside methods like steganography to hide the data they exfiltrate. The layered concealment makes it extremely difficult for an adversary to discern what is really happening, even if they manage to intercept some communication.
This relates to Risk Assessment.
Operational Ephemerality: Minimizing Data Retention
Operational ephemerality is perhaps the most radical application of OPSEC in the world of APTs and intelligence agencies. The idea is that data should exist only for as long as it is needed, nothing should be retained longer than necessary. This practice minimizes the risk of data being intercepted, analyzed, or exploited by adversaries. APTs often use temporary infrastructures, such as short-lived command-and-control servers or ephemeral malware that is deleted after use, to limit their exposure. The shorter the lifespan of the data or operation, the less chance there is for it to be discovered or exploited.
Similarly, intelligence agencies often rely on short-term data retention strategies. Covert operatives might only use certain communications channels for brief periods, ensuring that there is no persistent data trail left behind. Once the operation has ended, all traces of it are erased, and no data is stored longer than necessary. For APTs, this can mean deleting malware or communications logs once their mission is completed, ensuring that even if systems are compromised, there is nothing left to link back to the actors involved.
This relates to Implementation of countermeasures.
Internal Discipline and Threat Awareness
While OPSEC is often associated with external threats, its success relies heavily on internal discipline. Intelligence agencies all recognize that internal vulnerabilities, whether from careless actions, predictable patterns, or weak OPSEC practices can expose an operation to detection. An OPSEC practitioner must ensure that every step, every tool, and every communication is in line with OPSEC principles. This requires self-awareness and constant vigilance to avoid mistakes that might compromise the mission. Similarly, intelligence agencies emphasize the importance of internal discipline to prevent agents from inadvertently revealing information that could jeopardize an operation.
For APTs, this internal discipline manifests as tight coordination among various members of the attack group. Every member must adhere to strict OPSEC rules to prevent leaks, and any deviation from the plan could expose the entire operation. Continuous monitoring and self-correction are integral parts of maintaining operational security.
“Becoming Unpredictable”
OPSEC is a mode of becoming unpredictable. It reorients an entity’s presence from a visible target to an imperceptible phenomenon. In other words, OPSEC involves dissolving the outlines of the self into informational ambiguity such that a breach is impossible simply because there is no coherent structure to breach. This is consistent with the resilience principles identified by NIST, where security is a race to stay ahead of the adversary through disruption and constant change in response to the ever-changing threat landscape.
In this respect, OPSEC is no longer merely a collection of tools but rather a mode of becoming. It confronts traditional notions of security and compels an organization or a person to reimagine informational presence in flux, evasive, and imponderable. By embracing the principles of OPSEC removal, fragmentation, and concealment, these organizations can better protect information in a manner consistent with the holistic approach to system security and resilience provided by NIST.
This is the doctrine of OPSEC applied to information security, not as a toolset but as a necessary modus operandi, a mode of thinking that changes perpetually the meaning of what it is to be secure.
“But this is a bit too theoretical, and maybe repetitive, isn’t it?”
It is, and it should be.
This theoretical underpinning is important because practical applications draw their strength from these very foundational principles. The transition from the visible to the non-visible is not an abstract concept but a strategy that plays out in the long run. All these methods contribute directly to evading surveillance and thwarting adversaries in ways that ensure exploitable signals either do not exist or are incoherent.
In addressing the practice aspects, the theory provides an integrative state of mind that helps individuals contemplate at a critical and proactive thinking level. Instead of being on the receiving end and having to counter threats, the opportunity to preclude even detection transforms the practical applications into an effortless embodiment of the philosophy of concealing. This ensures that OPSEC is not only a tactic but basically an integral part of the way in which the operation remains as secret as possible.
Why OPSEC’s Doctrinal Approach Works.
OPSEC is Context-Driven, Not Just Rule-Based
A key distinction between OPSEC and traditional security frameworks lies in its flexibility. While effective in structured environments, such frameworks often lack adaptability to dynamic, high-risk contexts.
In contrast, OPSEC thrives in diverse and unpredictable environments. It emphasizes understanding the specific operational context, which involves analyzing the nature of adversaries, the value of protected information, and the tactics employed against it. For activists, or even individuals navigating surveillance by adversarial governments, OPSEC extends beyond technical tools to encompass patterns of communication, online behavior, and physical movement. Unlike frameworks that tend to impose static security rules, OPSEC adapts security measures to the situation at hand, making it indispensable in environments where threats constantly evolve.
OPSEC Encourages Long-Term Strategic Thinking
Bruce Schneier famously remarked, “Security is a process, not a state.” This philosophy is central to OPSEC, which emphasizes managing patterns over time rather than focusing solely on isolated vulnerabilities. A recurring principle in military and intelligence practices, echoed in the book Left of Bang by Patrick Van Horne and Jason Alley, is the importance of anticipation acting before the threat materializes. OPSEC builds on this by training practitioners to consider long-term risks, such as behavioral patterns that may inadvertently reveal critical information to adversaries.
For instance, while encryption protects the content of communications, OPSEC teaches practitioners to safeguard the context, the metadata, timing, and channels of communication. An individual who consistently uses the same platform at the same time might unwittingly reveal patterns that adversaries could exploit. OPSEC, therefore, is about shaping behaviors to remain unpredictable, reducing the overall attack surface across time.
OPSEC Focuses on Human Behavior and Operational Patterns
OPSEC is unique in that it concerns itself with more than just the technological tools and techniques employed in securing information. It realizes that security is inextricably linked with human behavior. Probably the most pervasive weakness in the security system is human error: careless handling of sensitive data, use of predictable passwords, or not understanding and managing behavioral patterns that lead to the divulging of critical information (as for ex. social engineering).
Traditional cybersecurity or privacy frameworks have often emphasized technologies such as encryption protocols or firewalls as the leading edge in protection.
Whereas these technologies are indeed indispensable, OPSEC realizes that security is also a matter of behavior. To APTs, this means knowing their operational patterns that might be easily predictable by adversaries, like routine use of specific devices, logins to accounts at the same time, or even the use of the same communication platform across different operations. By integrating human behavior into the security process, OPSEC enables practitioners to predict with accuracy exactly how adversaries can leverage such human patterns. The adversary knows, for example, what time each day a certain entity accesses a particular chat application and then uses that insight to map vulnerabilities. Giving users insights into how their behavioral pattern can be compromised, OPSEC offers one far greater degree of protection: anticipating the attack instead of passively protecting digital assets.
OPSEC Enables Dynamic Risk Assessment and Adaptation
Perhaps the most relevant element of the OPSEC doctrine is that of dynamic, ongoing risk assessment. Most traditional frameworks are focused on controls and checklists. Frameworks are designed to enable the simplification of complex jobs and provide structured tools that make them accessible to everyone, which makes frameworks accessible to anyone, disregarding their skills.
On the other side, OPSEC requires quite high competency because the operation deals with sensitive information, risk management, and intensive security measures. A good understanding of threats, vulnerabilities, and mitigation techniques is required in addition, as mistakes that happen in OPSEC may lead to dramatic consequences, such as data compromise or system compromise. These frameworks often fall short in accounting for changes within the nature of threats. In contrast, OPSEC embodies an ongoing process of risk assessment and adaptation in encouraging continuous reflection about vulnerabilities, the nature of adversaries, and the changing operational environment.
For instance, the OPSEC practitioner does not just assess the risks of surveillance or infiltration once and moves on. They must make regular reassessments considering new intelligence, emerging threats, and changes in personal or operational behaviors. It may include reevaluation of vulnerabilities concerning changes in technology, such as new ways of hacking or changes in government surveillance tactics, and personal habits, such as changes in geographic location or the use of different digital tools. OPSEC puts a person into a state of continuous evaluation of themselves and risks, so that in case one threat vector has been neutralized, other potential risks have not been overlooked.
OPSEC Prioritizes Actionable and Proportional Security Measures
Another significant benefit of OPSEC’s doctrinal approach is its emphasis on proportionality and actionability. Instead of trying to impose a one-size-fits-all collection of rules that must be followed in every circumstance, OPSEC invites practitioners to consider the likelihood and impact of several types of threats and to adopt countermeasures proportional to the risks they face.
This prioritization of risks over theoretical security principles makes OPSEC much more flexible and practical.
For example, someone operating in a high-risk environment-say, under a politically repressive regime will pay more attention to immediate threats, such as surveillance or data interception, and will take more intensive measures, like encryption or using secure communication networks. In contrast, the actor in a less hostile environment may want to consider other types of risk, such as the leaking of data due to careless behavior or tracking via predictable digital footprints. OPSEC enables everyone to make appropriate, considered decisions based on the actual threats.
OPSEC’s Provides Redundancy and Flexibility
A cornerstone of OPSEC is the concept of defense in depth, a strategy borrowing from military doctrine to establish redundant systems and techniques to ensure that in the failure of one layer, another remains in place. This is particularly important when highly sophisticated adversaries are encountered, such as state-sponsored actors or advanced hacking groups, who may try several methods to breach security.
Instead of depending on a single tool or technique, for instance, a VPN to mask one’s identity, OPSEC encourages the use of a multi-layered approach.
In the case of an attacker, this would involve using the Tor network, use of VPN/Proxies, change of routines to avoid surveillance, and finally, using secure hardware such as burner phones or encrypted laptops. The idea is that no single point of failure can lead to exposure, and even if an adversary compromises one layer of security, others remain intact to maintain operational integrity. This redundancy provides flexibility to adapt as new threats arise, which is critical in environments where technology, surveillance tactics, and adversary methods evolve constantly.
Conclusion.
In short, OPSEC doctrine is something that cannot be overlooked in today’s emerging threats, which call for increasingly sophisticated and adaptive strategies toward information security. Evolving from a toolset into a strategic mode of existence, OPSEC emphasizes the need for change.
These doctrinal principles with the NIST system security engineering framework can definitely assist organizations and people in upgrading their defense mechanisms against adversaries. Focus on the pattern of behavior, constant updating with the developments of threats, and multilevel defenses do mean a more proactive and long-term solution to today’s complex, almost unforeseeable security risks.
The next part will discuss current events and historical cases of agencies being exposed or individuals getting identified.
I’ll present the patterns on the ways they get exposed and why they get caught.
References:
OPSEC Manual (DoD Directive 5205.02): https://www.esd.whs.mil/Portals/54/Documents/DD/issuances/dodm/520502m.pdf
DTIC: https://apps.dtic.mil/sti/pdfs/AD1038572.pdf
DNI: https://www.dni.gov/index.php/ncsc-what-we-do/operations-security
NIST: https://csrc.nist.gov/files/pubs/sp/800/160/v2/ipd/docs/sp800-160-vol2-draft.pdf, https://www.nist.gov/, https://www.nist.gov/cyberframework
MITRE: https://attack.mitre.org/
ISO: https://www.iso.org/standard/27001
ZERO TRUST MODEL: https://www.microsoft.com/en-us/security/business/zero-trust








